A safe way to protect a place from hackers
Most people think that their website has nothing important to do with hacking. A hacker can compromise a website so that it can be used to transmit spam or as a temporary server to store illegal files. Hackers use automated scripts to break the Internet in an attempt to exploit software vulnerabilities.
The server operating software and any support software should be updated regularly. Any software vulnerabilities allow hackers an easier hole to manipulate and manifest their bad motives.
If the hosting company manages your website, you do not have to worry because the host company should take care of the security of the website. All third-party applications need to be updated regularly to apply new security patches.
The site administrator should be careful about the information displayed in your error messages.
Provide users with only limited errors to make sure they do not divulge secret information on your servers such as passwords.
Also Read: Fun Apps And Websites You Should Check Out In 2021
How to use passwords
You must use complex passwords to access the server or administration. Users should also be encouraged to use strong passwords to protect their accounts.
The combination of uppercase, lowercase letters, numbers, and special characters represent a secure password. Passwords should be stored using a scatter algorithm. Website security can be improved by using a new and unique salt per password.

To prevent hacking attempts, it is recommended that you avoid direct access to transferred files. Each file uploaded to your site should be stored in a separate folder outside of Webroot. You should create a different script to download the files from the private folder and use them in the browser.
Create complex passwords. The longer and more complex the password, the harder it will be for hackers to crack it. This greatly prevents password attacks. Use a unique password for each account.
Using a single password for multiple services is dangerous – if only one of these services violates data and your password is compromised, hackers can (and will) access your other accounts. You can prevent this by using a different combination of username and password to log in anywhere.
Use a password manager. Don’t panic if you don’t remember a million different combinations of usernames and passwords! Password Manager is a tool that stores and automatically fills in your credentials for various services, allowing you to create complex passwords without having to remember them all.
The only password you will need to remember is the “master” password that unlocks your encrypted password vault.
A good password manager is a reliable and secure place where you can store all your account information. Then, there are additional features such as password sharing that separates good and bad password managers, regardless of their ability to store data.
The least that a password manager needs to have is auto-complete, a master password, and a couple of other basic things.

When choosing a password manager, be sure to select one that is compatible with all your devices. Most web browsers have built-in password managers that store your passwords, making it easy to populate them automatically as you browse the web. Never give a password to anyone.
This is obvious advice, but one that needs to be repeated. Not only would you not give it to friends and family, but you should refrain from giving it to anyone who claims to be a computer technician.
Change passwords often. In addition to keeping your password secret, you should change passwords on different accounts and devices at least once every six months.
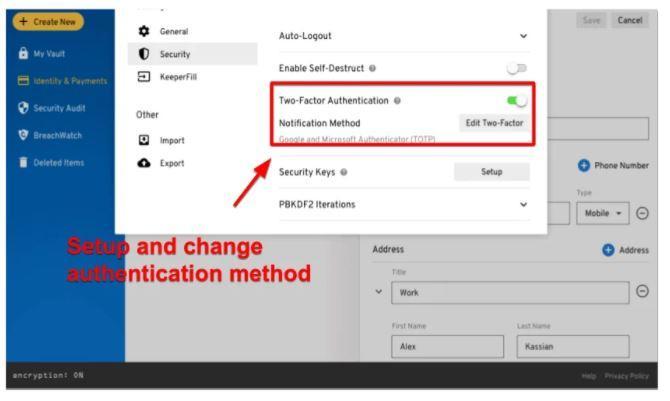
Use two-factor authentication
Two-factor authentication requires that you enter the code sent to you via text message or other services before you can log in to your account. If a hacker does not hold your phone in his hand when trying to access your account, he will not be able to complete the login process if two-step authentication is enabled.
Avoid using the correct answer for security questions. When asking security questions (like “What’s your mother’s maiden name?”), Don’t use the right answers.
Hackers can easily find out your mother’s maiden name or which street you grew up on. Instead, make the answers incorrect, or better yet, make them like passwords and don’t base the answers on the questions at all.
You must be on the official website when entering passwords. Identity theft scams are cases in which a malicious page pretends to be a social media or bank account login page. These types of scams are one of the easiest ways to hack.
Check out when you’re done. This is especially important when using a public or shared computer. Simply closing the browser window or laptop cover is not always enough, so be sure to click (or tap) your account name and select Logout (or Logout in some cases) to log out of your account manually.
Also Read: What Is The Best Mobile Spy App And How To Use It?
Protection of information privacy
Although many of us think that they have nothing to hide, when it comes to information privacy, for example. privacy of data related to the health condition, financial condition, political activity, residence, or family condition of an individual, the question arises as to how much power an individual has and what protection mechanisms are available to us in case of unauthorized collection of information.
To avoid confusion, we are talking about privacy protection at the level of collecting, storing, and processing information without our consent.
It is very difficult to achieve and maintain an enviable level of privacy and security in networks that have constant access to high-speed internet.
Once you embrace the principles of secure access and adhere to the rules, you will enjoy a work environment that does not reveal sensitive information that can later be misused, while the functionality will remain the same, and in many cases facilitated and improved.
In the times in which we live, we are witnessing the relentless struggle of the individual for the protection of privacy. We are overwhelmed by commercials, which are also the perfect tool for data collection and privacy violations.
Modern tracking algorithms allow you to link all the data and habits of users online in one profile, which compromises all your sensitive data and makes it available to companies and third parties without valid knowledge and approval.












+ There are no comments
Add yours